Overview
Runners are used by the Orchestrator to execute Terraform/OpenTofu modules securely inside your own infrastructure.
The Orchestrator will launch a runner to execute a deployment into a specific environment. Runners limit the blast radius as you can have as many runners defined as needed and have e.g. different runners for different network segments or permission sets.
There are different runner types to support executing runners on specific kinds of compute, like Kubernetes clusters or serverless container runtimes. Each runner is configured to use a particular instance of such compute.
A runner is either launched by the Orchestrator itself if the target compute is reachable for it, or by an agent running in the target infrastructure and polling the Orchestrator for deployment events.
In addition, a runner uses a particular state storage to maintain Terraform/OpenTofu state in between invocations.
Basic example
This example creates a runner for execution on a GKE cluster and using a state storage in the runner namespace. It then creates a runner rule for that runner.
resource "platform-orchestrator_kubernetes_gke_runner" "my-gke-runner" {
id = "my-gke-runner"
description = "GKE runner for my-cluster in europe-west3"
runner_configuration = {
cluster = {
name = "my-cluster"
project_id = "my-gcp-project"
location = "europe-west3"
internal_ip = false
auth = {
gcp_audience = "//iam.googleapis.com/projects/123456789012/locations/global/workloadIdentityPools/my-wif-pool/providers/humanitec-runner"
gcp_service_account = "humanitec-orchestrator-runner@my-gcp-project.iam.gserviceaccount.com"
}
}
job = {
namespace = "humanitec-runner"
service_account = "humanitec-runner"
}
}
state_storage_configuration = {
type = "kubernetes"
kubernetes_configuration = {
namespace = "humanitec-runner"
}
}
}
resource "platform-orchestrator_runner_rule" "my-gke-runner-rule" {
runner_id = platform-orchestrator_kubernetes_gke_runner.my-gke-runner.id
project_id = "my-project"
}
Runner config file gke-runner-config.yaml:
description: "GKE runner for my-cluster in europe-west3"
runner_configuration:
type: kubernetes-gke
cluster:
name: my-cluster
project_id: my-gcp-project
location: europe-west3
auth:
gcp_audience: //iam.googleapis.com/projects/123456789012/locations/global/workloadIdentityPools/my-wif-pool/providers/humanitec-runner
gcp_service_account: humanitec-orchestrator-runner@my-gcp-project.iam.gserviceaccount.com
job:
namespace: humanitec-runner
service_account: humanitec-runner
state_storage_configuration:
type: kubernetes
namespace: humanitec-runner
Create a runner using this configuration:
# Create the runner
hctl create runner my-gke-runner [email protected]
# Create an empty runner rule that will always match
hctl create runner-rule --set=runner_id=my-gke-runner
Configuration
A runner configuration consists of these elements:
Refer to the resource schema of each individual *-runner resource in the Terraform or OpenTofu provider documentation.
Extended example
resource.tf
(view on GitHub )
:
resource "platform-orchestrator_kubernetes_agent_runner" "my_runner" {
id = "my-runner"
description = "runner for all the envs"
runner_configuration = {
key = <<EOT
-----BEGIN PUBLIC KEY-----
MCowBQYDK2VwAyEAc5dgCx4ano39JT0XgTsHnts3jej+5xl7ZAwSIrKpef0=
-----END PUBLIC KEY-----
EOT
job = {
namespace = "default"
service_account = "humanitec-runner"
pod_template = jsonencode({
metadata = {
labels = {
"app.kubernetes.io/name" = "humanitec-runner"
}
}
})
}
}
state_storage_configuration = {
type = "kubernetes"
kubernetes_configuration = {
namespace = "humanitec"
}
}
}
hctl create runner my-gke-runner [email protected]
where runner-config.yaml is:
# Optional description
description: GKE runner for my-cluster in europe-west3
# Runner configuration
runner_configuration: {}
# Runner type
type: kubernetes-gke
# Further properties are depending on the runner type
# ...
# State storage configuration
state_storage_configuration:
type: kubernetes
# Further properties depending on the state storage type
The properties to set for the runner configuration and state storage configuration vary by their type. Refer to the individual sections for each runner type and state storage type to find the available configuration options and examples.
Runner types
Available runner types are:
State storage types
Available state storage types are:
Compatibilty matrix
Not all runner types can technically use every state storage type. The compatibility matrix shows the supported combinations.
| State storage type ➡️ Runner type ⬇️ |
kubernetes | s3 | gcs | azurerm |
|---|---|---|---|---|
| kubernetes | ✅ | ✅ | ✅ | ✅ |
| kubernetes-agent | ✅ | ✅ | ✅ | ✅ |
| kubernetes-eks | ✅ | ✅ | ✅ | ✅ |
| kubernetes-gke | ✅ | ✅ | ✅ | ✅ |
| serverless-ecs | ❌ | ✅ | ❌ | ❌ |
Manage runners
Manage runners using the hctl CLI:
hctl create runner my-runner [email protected] # Create a new runner
hctl get runner my-runner # Get details on a runner
hctl get runners # List all runners of your organization
hctl update runner my-runner [email protected] # Update a runner with a runner config
hctl delete runner my-runner # Delete a runner
Runners and environments
Each environment must have exactly one runner linked to it as a result of the runner rules in order to perform a deployment into that environment.
The runner creates the link to the Terraform/OpenTofu state for that environment through its state storage configuration.
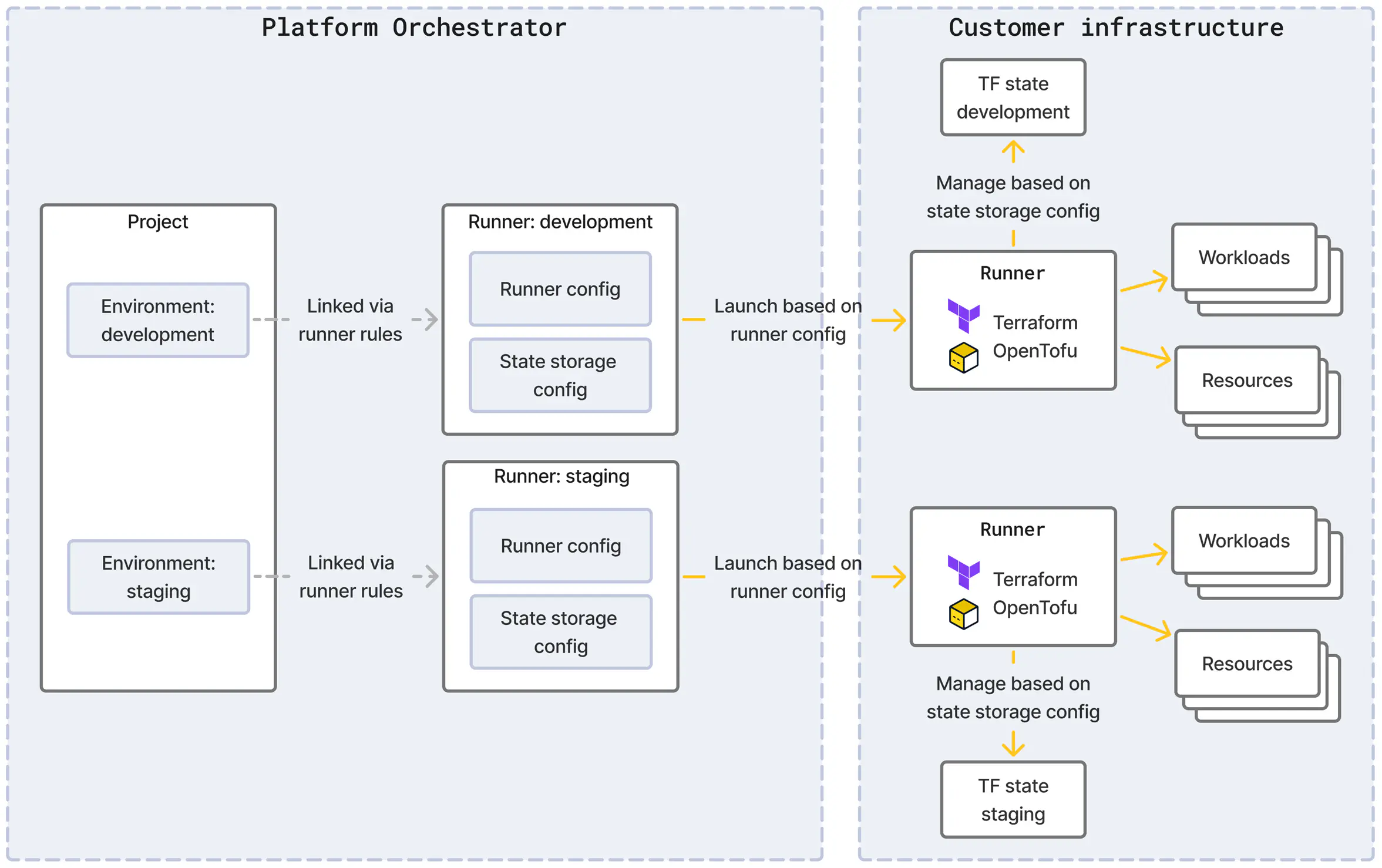
The environment remains linked to a runner even when the runner rules change until the refresh_runner API is called on the environment. This is because changing a runner may lead to dropping access to the previously used Terraform/OpenTofu state and thus a potentially undesired destruction of resources.
Refresh the runner for an environment
An environment remains linked to a runner even when the runner rules change. Execute the refresh_runner command on the environment to re-assign a runner based on the current runner rules.
Use the dry_run flag to test the result of the command without applying any change.
curl https://api.humanitec.dev/orgs/my-org/projects/my-project/envs/my-environment/actions/refresh_runner \
-X POST \
-H "Authorization: Bearer ${HUMANITEC_AUTH_TOKEN}" \
-H "Content-Type: application/json" \
-d '
{
"dry_run": false
}'
If a runner could be identified for the environment, the command will return that runner’s id.
If no runner could be identified, the command will return an error and the environment will remain associated with the previous runner.
Runner agent
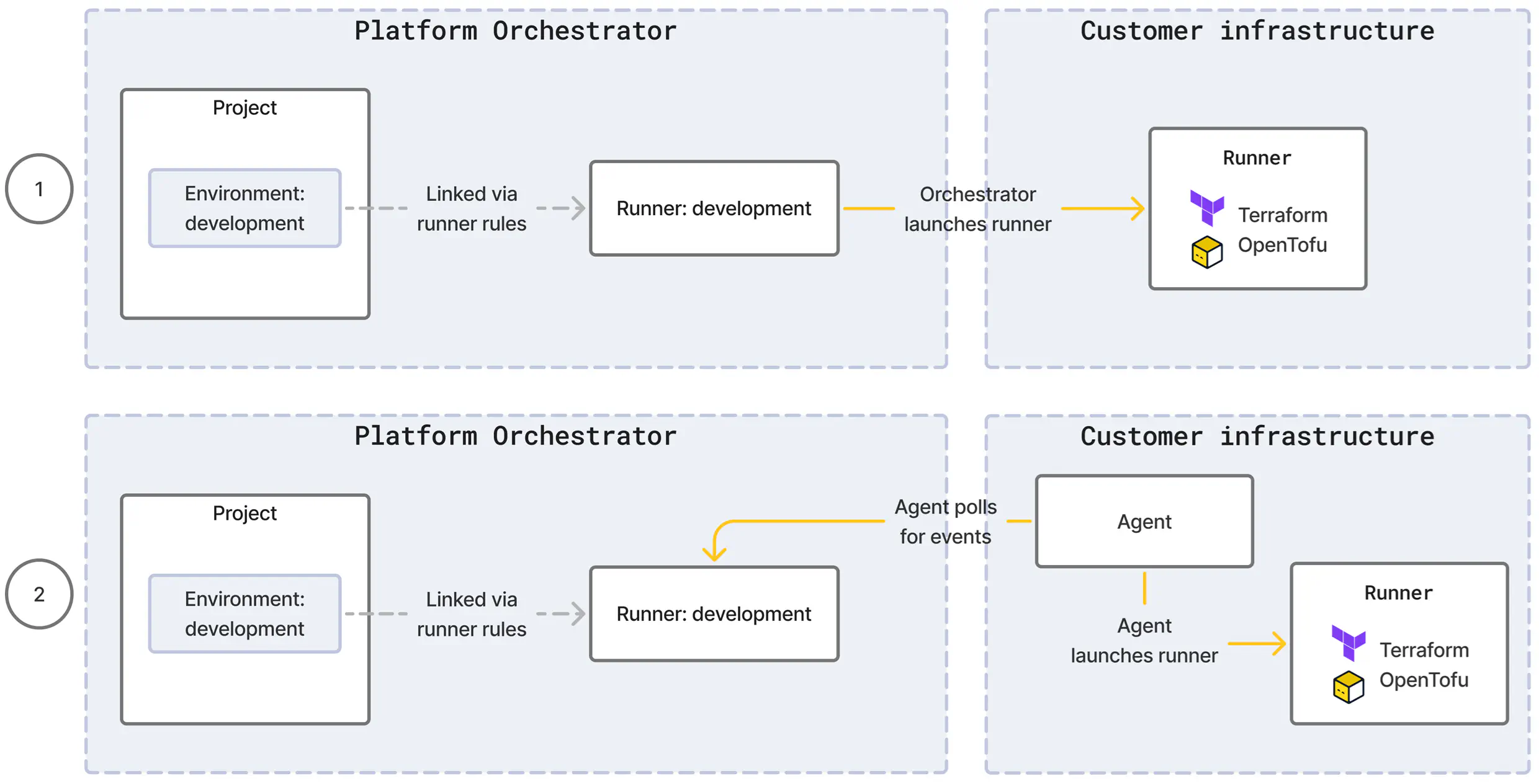
For each runner type, the Orchestrator will either launch runners itself or make use of an agent component to do so.
Direct: If the target compute for the runner execution is reachable for the Orchestrator, it can create a runner itself. This is true e.g. for runner types using a cloud-based service where the cloud API is publicly accessible, and shown as scenario (1) in the diagram below.
Agent: If the target compute for the runner execution is not reachable for the Orchestrator, the runner type comes with an agent which you install in your infrastructure. The agent creates an outbound, encrypted channel to the Orchestrator and continuously polls for deployment events. For each event, the agent launches a runner and relays the results back to the Orchestrator. This is shown as scenario (2) in the diagram below.
Runner image
A runner is based on a container image which is pulled from the public source ghcr.io/humanitec/humanitec-runner by default, using one of the recent versions. The most current available version is 1.10.3.
You may need to use a custom container image to:
- Pin an image to a specific version
- Pull from ECR or other private registries
- Use an image with custom tooling
The runner execution environment, e.g. a Kubernetes cluster, serverless runtime, or other compute, must be able to pull images from that source.
If you wish to pin the runner version or self-host the image in your own registry and have the runner pull from there, you can override the image property in your runner configuration.
Kubernetes runner configuration for image override
This snippet shows how to configure the image source as well as related settings like imagePullPolicy and imagePullSecrets from the PodSpec . Omit them if not required.
The container name must be set exactly as shown.
runner_configuration = {
job = {
pod_template = jsonencode({
spec = {
containers = [
{
name = "main"
image = "my-own-registry.com/humanitec/humanitec-runner:vx.y.z"
imagePullPolicy = "IfNotPresent"
}
]
imagePullSecrets = [
{
name = "regcred"
}
]
}
})
}
}
runner_configuration:
job:
pod_template:
spec:
containers:
- name: main
image: my-own-registry.com/humanitec/humanitec-runner:vx.y.z
imagePullPolicy: IfNotPresent
imagePullSecrets:
- name: regcred
Serverless ECS runner configuration for image override
This snippet shows how to configure the image source in the job configuration.
runner_configuration = {
job = {
# Custom container image name
image = "my-own-registry.com/humanitec/humanitec-runner:vx.y.z"
# See other required properties in the ECS runner docs
}
}
runner_configuration:
type: serverless-ecs
job:
# Custom container image name
image: my-own-registry.com/humanitec/humanitec-runner:vx.y.z
# See other required properties in the ECS runner docs
...
Create a custom image
Minimal Docker image
Your custom image should inherit from the humanitec-runner image to ensure compatibility:
# Use a pinned version of the official Humanitec runner
FROM ghcr.io/humanitec/humanitec-runner:vx.y.z
# Add your customizations here (certificates, tools, or configurations as needed)
...
# Everything else is inherited:
# - Tools, configurations (eg. OpenTofu)
# - Entrypoint: ["/opt/runner/runner"]
